-
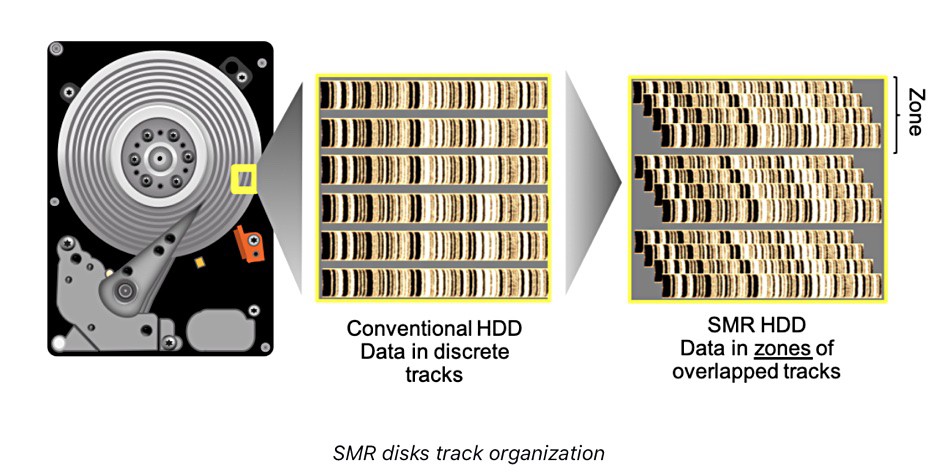
The nightmare of Shingled Magnetic Recording for NAS drives
IT systems are like onions, they have layers. And when the bottom-most layer fails, everything follows. This is the story of our experience with WD Red hard disk drives at Hello Watt, and how even while following good practices of system administration, deceptive advertising can cause your business to lose weeks of work.
-
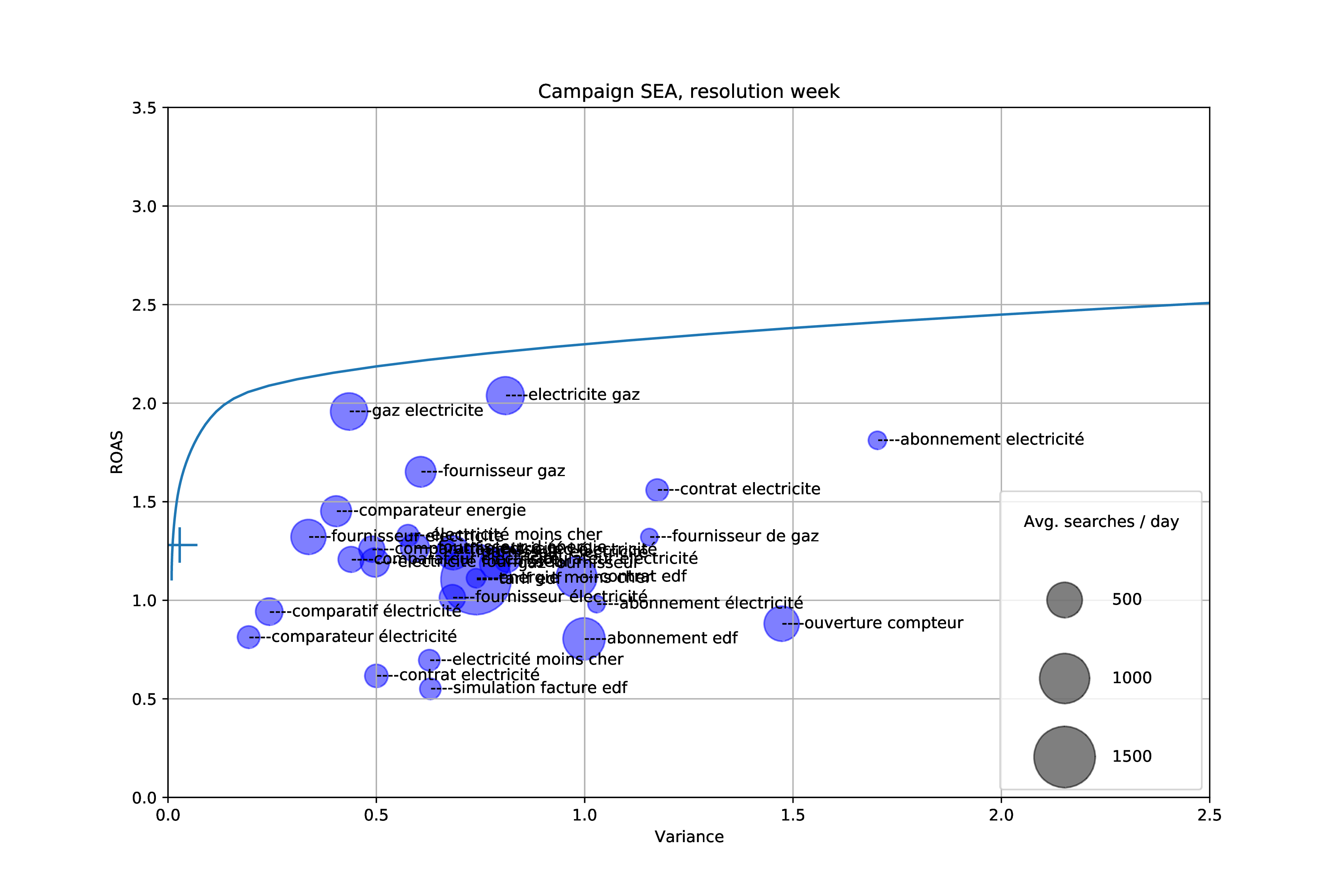
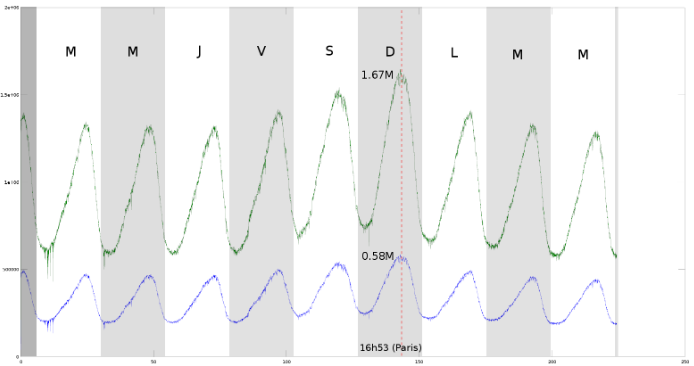
Optimization of Google Ads bidding taking into account our influence on the market
In this article, we give a brief overview of the Google Ads platform from the point of view of an advertiser as well as its available performance indicators and controls. We show how a simple portfolio optimization method indicates we can increase our ad returns significantly. Finally, we design a more complex model that takes…
-
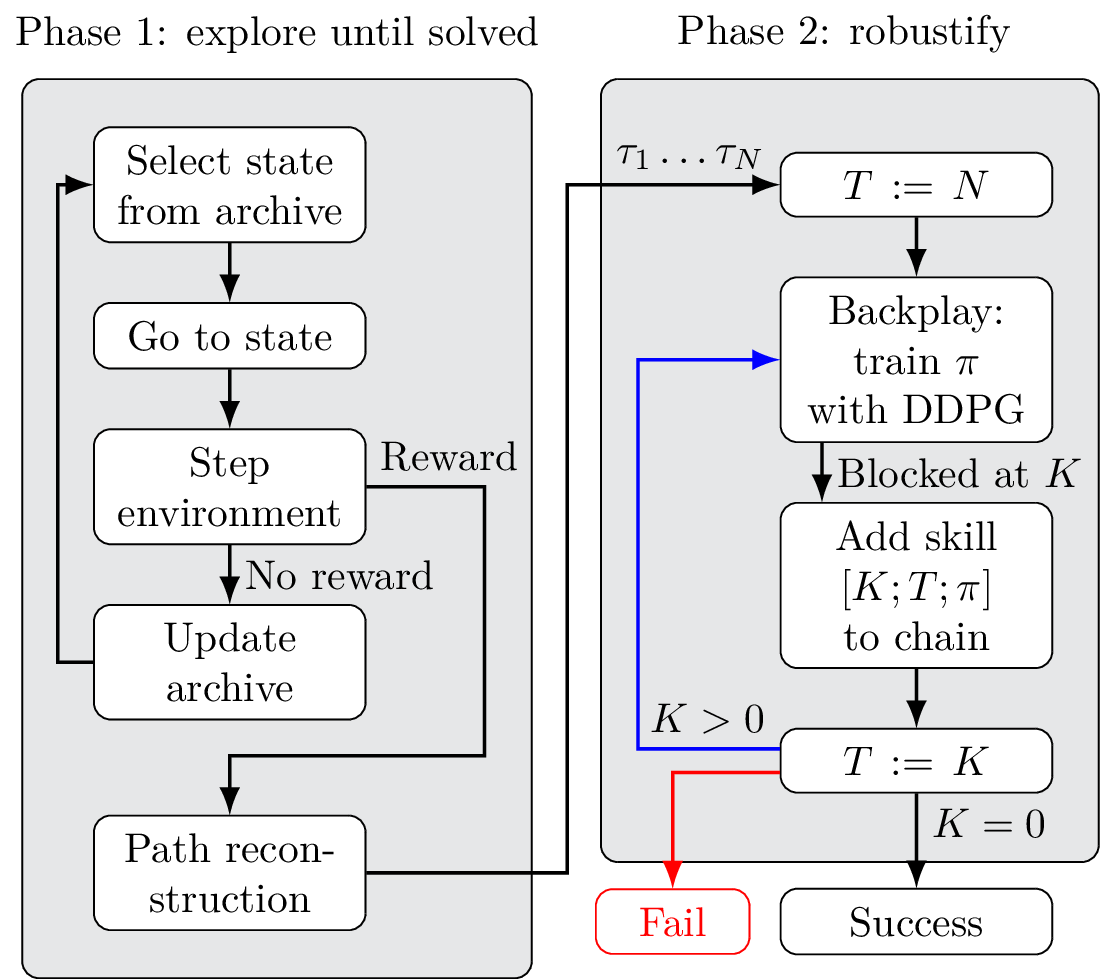
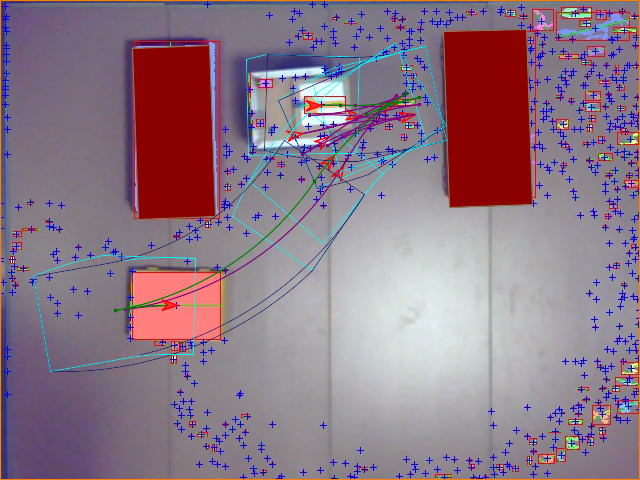
PBCS: Efficient Exploration and Exploitation Using a Synergy between Reinforcement Learning and Motion Planning
The exploration-exploitation trade-off is at the heart of reinforcement learning (RL). However, most continuous control benchmarks used in recent RL research only require local exploration. This led to the development of algorithms that have basic exploration capabilities, and behave poorly in benchmarks that require more versatile exploration. For instance, as demonstrated in our empirical study,…
-
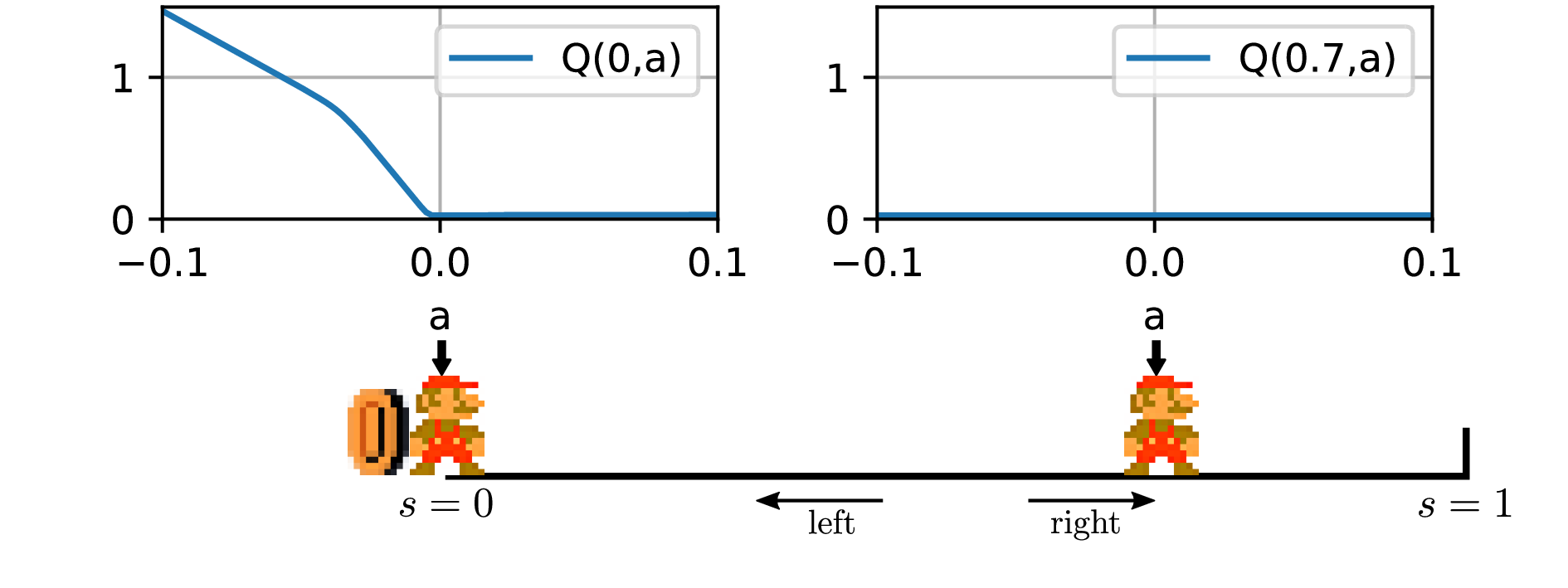
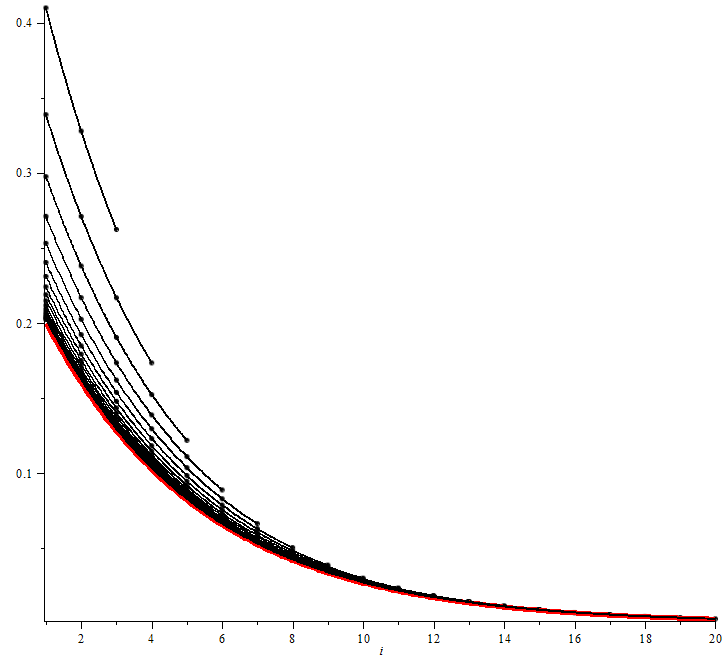
The problem with DDPG: understanding failures in deterministic environments with sparse rewards
In environments with continuous state and action spaces, state-of-the-art actor-critic reinforcement learning algorithms can solve very complex problems, yet can also fail in environments that seem trivial, but the reason for such failures is still poorly understood. In this paper, we contribute a formal explanation of these failures in the particular case of sparse reward…
-
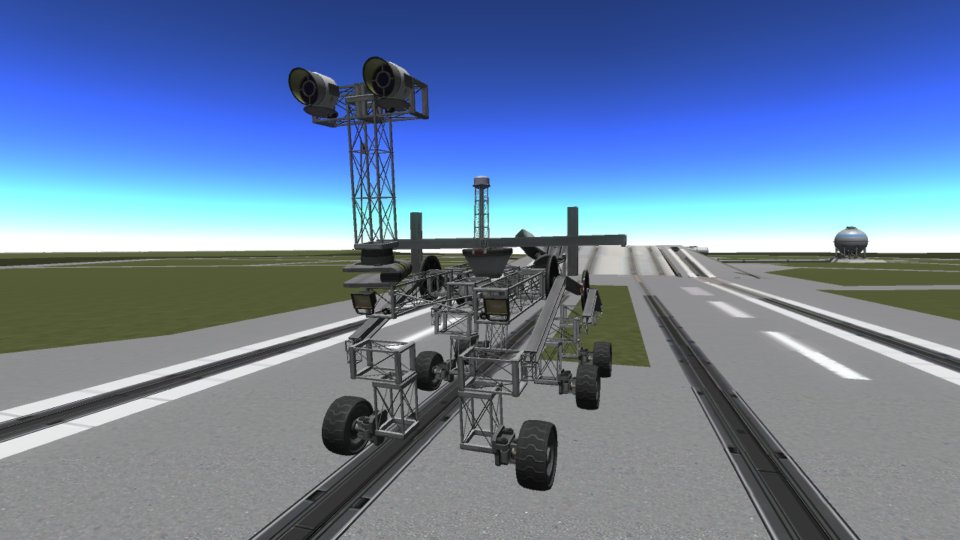
Curiosity rover in Kerbal Space Program with working rocker-bogie suspension and differential
It’s always a privilege doing what I love for a living. This past two months I’ve been on Curiosity’s next-of-kin at the NASA Jet Propulsion Lab in Pasadena. On a boring evening, I started to try making a working Curiosity rover in Kerbal Space Program. The main two challenges were the rocker-bogie suspension and its…
-
Parking avec la voiture de Reeds et Shepp
Dans le cadre d’un projet de cours, nous (\, ^ et moi) avons construit un robot capable de se déplacer sur une surface plane en présence d’obstacles grâce aux courbes de Reeds et Shepp. Ces courbes sont en particulier utilisés pour la planification du mouvement lors du mode parking automatique sur certaines voitures (créneaux automatiques).…
-
Chaînes de Markov et files d’attente
Les chaînes de Markov sont un outil mathématique permettant de modéliser l’évolution d’un système dont l’état au temps t+1 ne dépend que de son état au temps t, et possédant un nombre fini d’états. Ce document s’intéresse à l’étude de l’évolution des systèmes à partir de leur matrice de transition. En particulier, on énoncera une…
-
Parcours de la DHT BitTorrent
Le programme effectue un parcours de la DHT le plus exhaustif possible (environ un million de noeuds) en partant du bootstrap “router.bittorrent.com” de BitTorrent.Le réseau ainsi découvert est stocké au format csv pour pouvoir être ensuite étudié à l’aide d’outils tels que Octave ou Matlab.Comme la taille des données que le programme traite est conséquente,…
-
Old-school WEP wifi hacking
This is a pretty old technique, often cited to demonstrate flaws in once-commonly-used security schemes. In this article you will learn how to attack a WEP access point (AP). You will need : I assume you are already familiar with linux and the general operation of wireless networks. Step 1 Start your wireless card in…
Guillaume Matheron
Data scientist, PhD in computer science